
This has really happened to an online team:
One of their Web Developers didn’t appear online at the usual time. She sent a message from her smartphone, saying that she had troubles with her PC, and that she would come online as soon as she fixed them.
Still, she appeared only the day after that event, sharing with the team the most unfortunate story. When she attempted to access the files on her PC, they were locked and encrypted.
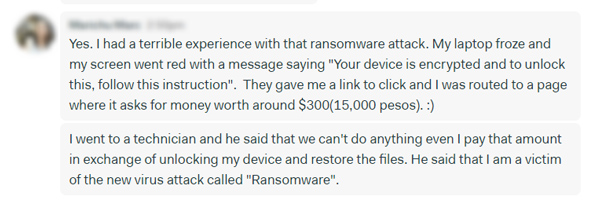
Every attempt to access them and do something about it failed and resulted in a message in which hackers that infected her PC demanded money in exchange for a password to unlock her PC.
This poor Web Developer spent an entire day with an IT technician in attempts to restore her system. They, eventually, succeeded, but it cost a lot of time and money. And not only that!
She was incredibly stressed! This computer was her livelihood and her means to support her family. To think that she could lose her job and the main tools of work drove her to tears.
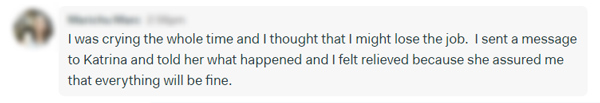
The scenarios that were running through her head were horrific and you should definitely try everything in your power to prevent this from ever happening to you.
What happened to this is called ransomware. This type of cyber attack is relatively new and it is getting quite common.
Where did the #ransomware epidemic come from, and what can you do?
https://t.co/lE44tBI9VS pic.twitter.com/Q4ppRz8f52— Fortinet (@Fortinet) October 5, 2017
Sounds scary, right? It is!
The worst thing about this is – this is far from being the only threat that can jeopardise the system of an online worker or any other type of Internet user.
Vicious hacker attacks can happen to anybody and it is a very big deal because they can hurt you and your company.
As you can see from the example above, even the professional, like this Web Developer, fell victim of a cyber attack. Moreover, even some of the biggest companies were breached by hacker attacks. Alibaba suffered an extensive attack from Chinese hackers while eBay had their databases hacked and data stolen.
Once a cyber attack happens to you or your store, the consequences can be devastating. You can lose data, money, reputation and all your efforts can go down the drain.
Still not scared? Take a look at the Norton’s article about The 8 Most Famous Computer Viruses of All Time. That can help you understand the seriousness of this threat.
Even if only one computer is infected in your online team, the virus can spread to the entire platform and incapacitate the entire company. It is your duty, as an online worker, to do your best to secure your own system and the system of your online employer.
So, what can you do?
The only thing you can do is arm yourself with as much knowledge as possible and do everything in your power to prevent these attacks.
In this lesson, we’ll talk about when you should suspect your computer has been compromised. We will then explain in more detail what types of threats lurk from the online world and then we will teach you how to prevent the attacks and protect yourself from them.
How to Detect if Your Computer Has Suffered a Cyber Attack?
When you catch a flu virus, you know it almost instantly. Your energy level drops, you probably get a runny nose and a fever. However, sometimes, it can pass by with a minimum of symptoms and you hardly realise you even had it.
Something similar happens when a computer is under attack. Some attacks are hardly noticeable, while others can be very disturbing. Just like with your own ‘malfunction’, there are several computer virus symptoms that you need to spot and look into.
Be concerned if your PC shows the some of the following behaviour:
– It works unusually slowly
– It executes commands you haven’t issued like printing, etc.
– Your system presents popup windows and messages
– Unexpected low space on your drives. Take a look at how it is done on a PC:
And, of course, on a Mac, as well:
– It presents high traffic on your network, even though you are not using it at the moment. Here are some articles that will teach you how to do that, and a very useful discussion with precious suggestions.
- How to Tap Your Network and See Everything That Happens On It
- How to monitor, measure, and manage your broadband consumption
- Sniffing network traffic for signs of viruses/spyware
Terry Cutler shows how to detect possible existing threats in his video. It involves a bit more advanced knowledge, but presented in a very easy way:
Here is a very useful episode of The Tech Guy where he talks with his listeners about signs and symptoms of being a victim of cyber attacks and even warning people not to be paranoid, either.
Learn even more by reading the following extensive articles on this subject:
- BlueSodium: 20 Common Computer Virus Symptoms With Solutions And Tips
- HEIMDAL Security:14 Warning Signs that Your Computer is Malware-Infected
It is not just your computer that can be hacked. Your email and other different accounts can be hacked, as well. If your email has been taken over, your friends and colleagues may report that they are getting suspicious emails from you. To check that, you can visit the HaveIBeenPwned website and let them check the account for you.
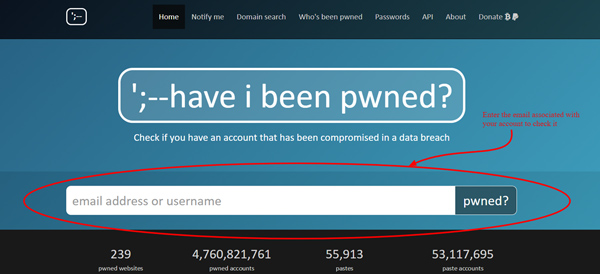
Their Twitter account is very active and it is useful to follow them, as you can learn a lot about the latest, current threats and prevent them before they happen to you.
New breach: Following their 2019 breach, 25M email addresses from MGM Hotels were shared on Telegram channels last week. Data included email and physical addresses, names, phone numbers and dates of birth. 86% were already in @haveibeenpwned. Read more: https://t.co/bRQ08QlM82
— Have I Been Pwned (@haveibeenpwned) May 29, 2022
New breach: Social media marketing company Preen[.]Me had 236k email addresses breached in 2020. Data also included names, usernames and links to social media profiles. 87% were already in @haveibeenpwned. Read more: https://t.co/x64T3aJBoa
— Have I Been Pwned (@haveibeenpwned) May 26, 2022
New breach: Amart Furniture had over 100k records breached from an AWS account last week. Data included email and physical address, names, phone numbers and bcrypt password hashes. 68% were already in @haveibeenpwned. Read more: https://t.co/JAnhTYPFVD
— Have I Been Pwned (@haveibeenpwned) May 25, 2022
New breach: Wendy’s in the Philippines had 52k email addresses breached in 2018. Data included names, email and IP addresses, physical addresses, phone numbers, job applications and MD5 password hashes. 81% were already in @haveibeenpwned. Read more: https://t.co/QzyDExcl4H
— Have I Been Pwned (@haveibeenpwned) May 24, 2022
So, how come some threats attack your very own PC and some of them attack your accounts? That is because there are different types of online threats. Let’s get you informed about the most common ones.
Types of Most Common Online Threats
Generally, you can classify all online threats into several categories. Here are some of the most common types of cyber attacks:
Some of those are more or less frequent when it comes to cyber threats to eCommerce companies. Still, you need to learn more about each of these threats and be prepared.
Let’s look into these several cyber threats more closely:
Malware
Malware or malicious software is a type of software that is created in order to attack your device, steal sensitive data like personal information, credit card numbers, etc, as well as to corrupt the devices in some way. There are different types of malware.
Usually, when people talk about computer viruses, they are actually thinking about malware. Viruses are just one type of malware.
To learn about different types, take a look at this video from the Kaspersky YouTube channel:
This quick video shows you all the basics that you need to know, but if you really want to go into depth and learn about the history of malware, its types and terminology, go ahead and read MalwareFox: List of Types of Malware.
Let’s put a word or two about the most common types of malware:
Virus is always in some sort of a file that you need to open yourself in order for it to infect your computer. It can be sent to you in a form of email attachment or even transferred via a USB drive.
MakeUseOf: The 7 Types of Computer Viruses to Watch Out For & What They Do
YoungUpStarts: 9 Types Of Computer Viruses That You Should Know About – And How To Avoid Them
Worms are much more malicious because they can infect your computer even if you don’t attempt to use any suspicious files. They use the weak spots of networks to hide and reach your computer if you are connected to such network.
Trojans infiltrate your computer in order to give control over your computer to somebody else. While viruses and worms can multiply themselves once they reach your system, trojans cannot do such a thing. On the other hand, they open your PC to other people and that means they can make serious damage to it.
Zoran Lalic presents a very new definition of Trojan Horse: SSL-encrypted threats. https://t.co/ptddXAhi15 #trojan #encryption pic.twitter.com/99yacmniM1
— TheAnalogies Project (@TheAnalogies) August 25, 2017
Rootkits are quite similar to Trojans as they have almost the same purpose – they give access to your computer to somebody else.
While Trojans simply “open the backdoor” to your PC and they are sometimes disguised as useful applications.
On the other hand, Rootkits can be considered more powerful as they are harder to detect and they attack root of your PC giving outsiders administrator access and control.
Remember the story from the beginning? We said that was an example of ransomware. That’s person’s computer was probably infected by some sort of a Trojan that gave the hackers the control over her computer.
ITProPortal: What is ransomware? Everything you need to know collects articles concerning latest trends in ransomware.
Spyware are computer applications that infiltrate your computer, but they don’t attack it. They steal your information. This can involve some of your personal data and even your credit card numbers and other sensitive information. One of the sub-types of spyware are keyloggers that record your keystrokes and steal your passwords and other data.
Adware are all those pesky pop-up ads that attack your computer. They display different ads to the user and slow down your computer by doing so.
Malvertising is a rather new term that signifies the process of introducing the malware to your PC via website that is good on its own, but contains malicious ads.
What is #Malvertising?#CyberAttack #Ransomware #Dataviz #Cloud #CyberCrime #Defstar5 #CyberSecurity #Industry40#InfoSec #AI #ML #Malware pic.twitter.com/wVVel60D50
— Joseph (@appwebtech) October 6, 2017
Bot originated from our need to give boring, repetitive tasks to machines or software. They are programs designed to complete simple, repetitive tasks. Good bots serve as web crawlers, for example, and they gather information about websites. Bad bots crawl into your computer, connect to central server and take control of your PC. A network of such infected computers is botnet.
If you want to learn in more detail how bots work read this article from Naked Security: How bots and zombies work, and why you should care.
Bug is usually a flaw in software. Usually, it is not a big deal and is easily fixed with a patch. However, it can be quite an issue if it is created in a piece of security software.
If you want to learn more about the subtle differences of these types of malware take a look at this article from Cisco: Viruses, Worms, Trojans, and Bots or Veracode: Common Malware Types: Cybersecurity 101.
Phishing
This is a type of cybercrime that includes hackers using emails or web pages that look like legitimate requests from your familiar sources to enter our login details, bank accounts and credit cards. This threat has become so widespread that there is a website dedicated to it – Phishing.org.
In order to protect yourself from the phishing attacks, it is important to understand different types of phishing. Take a look at this infographic to learn more.
Don’t worry if you recognise a phishing email in your inbox. If you don’t open it, it cannot harm you. Learn from the examples found in the tweet below about the phishing attempts that targeted small businesses.
#Phishing scams are on the rise, but the more you know…. https://t.co/tRPQkhFHFk #smallbiz #cybersecurity
— Clarity (@claritytel) October 6, 2017
If you are still curious, read a great article from ZDNet: What is phishing? How to protect yourself from scam emails and more.
If you have 10 minutes to spare, you can also take a look at this funny video that features James Veitch answering some of the fraudulent spam emails. It will show you the usual style in which these emails are written.
Flooding
In more technical terms, this type of attack is called Distributed Denial of Service attack (DDoS). Your website is designed to receive a certain amount of traffic. If you overflow the website with too much traffic it will freeze and shut down.
In this way, your eCommerce website cannot work and earn money! There are also combinations of DDoS attacks and ransom as in the example below:
#DDoS attack warning emails are the scams. ESET’s Anti-Spam & Network Protection features will protect your devices.https://t.co/2ePDOxs2Kf pic.twitter.com/Vxp949nxx0
— ESET Australia (@esetaustralia) September 26, 2017
These types of cyber attacks should be dealt with by professionals, but you should know about them and the way they work, so you can try and prevent them or at least realise what is happening so you can ask for help.
Man-in-the-Middle attack
We already explained in the lessons about the Internet how it works. Your computer communicates with remote servers every time you use it.
Man-in-the-middle attacks are actually all interceptions of such communication. In that way, they can steal the information such as passwords and other sensitive data which can be used to hurt the eCommerce store.
As you can see, these types of attacks are frequent when using public Wi-Fi networks. It is very important that eCommerce employees understand this, because they can, sometimes, be in situation to work in public places, such as cafes.
These are the basics of cyber attacks every eCommerce employee should be aware of. Risking the security of your own computer means compromising the security of the entire eCommerce company you are employed with.
Being a responsible eCommerce employee means preventing such threats because the security chain of an entire eCommerce store is just as strong as its weakest link.
Here are some interesting numbers of security threats for 2017.
The top cybersecurity threats of 2017 #ransomware #infosec #Hacking #malware #IoT #phishing #DDoS
@Fisher85M @chboursin HT @Socialfave pic.twitter.com/5UckZaS8J3— Sabelo M Ndzakane (@SabeloMario) October 9, 2017
You have now learned about some of the most common cyber threats, but hackers are getting more and more creative with each year.
There are many more subtypes and combinations of cyber threats and if you want to know more about them, read the following articles and check out the resources.
- McSweeney & Ricci: 5 Different Types of Cyber Attacks and How They Affect Your Business
- Rapid: Common Types of Cybersecurity Attacks
Proper Prevention and Protection
The best weapons in your fight against hackers and cyberattacks are knowledge and prevention. It is your duty as an online employee to stay on top of things when it comes to cyber security.
Being secure online means two things – you should follow the cybersecurity guidelines posed by your employer and you should do your best to keep your own computer secure.
Why?
We already mentioned that your computer can serve as a gate for a hacker to enter the entire eCommerce platform, so your PC needs to be airtight.
Here are some of the steps you should take in order to prevent cyber attacks:
Passwords
Password management is very important for online teams. Strong and frequently changed passwords increase online security. However, while password protection for an eCommerce store is a matter for your employer, you need to make sure you, yourself, protect your computer with strong passwords.
Read here how: McAfee Blog: 15 Tips To Better Password Security
Once you protect your own computer, deal with the passwords, as well. Don’t share them and always use the recommended password management software.
Sharing Information
Usually, when it comes to sharing sensitive information within the team, different people have different accesses. Make sure you never share this type of information with people who are not on your level of access.
Your online employer knows why they gave that access to some people and not to the others, so respect that decision.
Recognising Possible Threats
Now that you know enough about malware and phishing, you need to protect yourself from those attacks and the first step is recognising them. You already know the symptoms of the existing threats, but let’s see what you can do to protect your computer.
Big Mike’s Blog: Learn to Recognize Suspicious Online Virus’s and Malware
Of course, when you talk about viruses, malware, phishing and other types of scams, you are thinking about online threats. However, don’t forget about the ‘good old’ real-life threats.
- Your computer may not be the only thing that contains a virus. It can also be your mobile phone, USB drive and other external discs that you use with your computer. ONLY use those that you are 100% sure are clean and malware-free.
- Don’t share your passwords and don’t let others use your computer that you use for work. You can never know their intentions or their ability to use it safely.
- Whenever possible, don’t use public Wi-Fi networks. MakeUseOf: 5 Ways Hackers Can Use Public Wi-Fi to Steal Your Identity warns about the possibilities for your PC to be compromised by using a public Wi-Fi.
- Always keep your system up to date. New updates are usually security patches that cover up weak spots in your system that were not known before.
- Use backup. Decide if you want to have all your work backed up on a cloud or on a physical drive. Lifewire suggests 5 Ways to Back up Your Data.
CNET: How to prevent malware and adware downloads
EMSI Soft: Spring clean your PC in 5 simple steps and prevent malware
Enigma Software: Important Steps to Prevent Malware Infection
Using Firewalls, Antivirus and Antimalware Software
In order to be safe, you need antivirus software and firewalls. These are two different types of software. Here is what antivirus and antimalware does and how they work:
Now that you know you need this type of software, here is a link that will help you decide make the best choice for yourself: 10TopTenReviews: The Best Antivirus Software of 2017 is regularly updated about current threats and protective software.
On the other hand, you also need a proper firewall for your protection. Here is what the firewall really is and what different types of firewalls are there:
If you are wondering what is the difference between the antivirus and firewall software – it’s easy. In simple words, a firewall screens the incoming and sometimes outcoming traffic to spot malware. Antivirus software scans the files that are already within the system in hope to weed out all the threats that are already there.
So, which one to choose? Both!
Here is a bit more about their differences and how you should have both of these protections for safe online work: It Still Works: Differences Between Firewall & Antivirus.
If you are curious how large companies prepare for cyber attacks, here is an interesting infographic with some numbers:
How large companies prepare for #CyberAttacks!#Cybersecurity #Firewall #hackers #Ransomware #IoT #infosec #DataSec #IoT #BIgdata pic.twitter.com/th8zHZvXba
— j@ydip Dob@riya – ☘ ⓈⓄⒸⒾⒶⓁ (@jaydippatel21) October 6, 2017
Now, you know when to suspect that something is wrong with your computer and what it can be. You also know how to protect yourself and your work and even how to prevent disastrous results of cyberattacks.
Armed with this knowledge, you are certainly an employee that understands the importance of online safety and has the skills to keep the team protected by protecting yourself.
In Summary
Keeping your computer safe from online threats is important, besides the obvious, because it is a way of keeping your entire company safe. Only one infected computer is enough to jeopardise the entire company.
The first thing you need to learn is how to detect if your computer is infected right now. Yes, now! While you are reading this! You can try and answer the following questions:
- Does your computer work at its usual speed?
- Do you see any unusual pop ups while browsing the Internet?
- Is your network unusually busy while you are not doing anything on it?
- Are there some programs that don’t work properly or entirely unknown programs on your PC?
- Are you running out of disc space at an unusually high speed?
If any of these questions has a positive answer, you need to run a full computer scan using good and reliable antivirus and antimalware programs.
However, even if you are not infected, you need to instal a firewall in order to prevent such occurrence. There are other steps that you can take to prevent attacks, as well. These include proper password management, careful sharing of the information, using only safe Wi-Fi networks for work and being extra cautious when it comes to USB drives.
If you fail to protect your computer, you can fall victim to different types of cyberattack that includes malware, phishing, flooding and man-in-the-middle attacks.
Malware is a broader term than the term virus that most people use. Malware are all viruses, trojans, worms, bots, bugs, rootkits and other similar software.
Phishing, on the other hand, is a type of threat that aims at the very user. It is an attempt to trick you into opening or installing a file that contains some sort of malware.
Flooding is an attack aimed at a website and it involves overburdening it with traffic so that it blocks and goes down. It can cost a lot of money.
Man-in-the-middle is just what it sounds – somebody between you and the server, spying on your communication and stealing sensitive data.
Now that you know all this, let’s check your knowledge and fortify it by the quiz below!
Frequently Asked Questions
1. Is malware the same as a virus?
a. Malware is a broader term. Viruses are malware but not all malware is viruses.
b. Malware equals virus.
2. What is the difference between a virus and a worm?
a. There is no difference.
b. Worms don’t have to be activated by the user.
c. Viruses don’t have to be activated by the user.
3. What is phishing?
a. A type of cybercrime that includes hackers using emails or web pages that look like legitimate requests from your familiar sources to enter our login details, bank accounts and credit cards.
b. Misspelled sport and recreational activity.
c. A name for the latest computer virus.
4. What is the difference between a firewall and antivirus software?
a. They are just two names for the same product.
b. The firewall prevents the threats from entering the system, while antivirus scans it to find the already existing infections.
c. Antivirus programs only kill viruses and firewalls burn worms.
